Ironchip Solutions for IT Managers
Effortless Control, Uncompromising Security.
Ironchip empowers IT managers to simplify identity management, enhance security, and reduce operational overhead. We eliminate the complexities of passwords, providing a seamless and secure experience for both IT staff and end-users.

Intrusion threat detection & response
Automated Defense, Reduced Operational Burden
Manually investigating and responding to fraud incidents is time-consuming and resource-intensive. Ironchip's location-based fraud detection automates this process, providing:
- Automated fraud detection and prevention: Identify and block fraudulent activity in real time, minimizing manual intervention.
- Reduced investigation time: Provides detailed forensic data to streamline investigations.
- Improved operational efficiency: Frees up security teams to focus on other critical tasks.
- Real-time Threat Visibility: Provides a clear overview of potential fraud risks.
- Automated Response Capabilities: Automatically blocks suspicious activity, minimizing damage.
- Reduced False Positives: Minimizes disruptions for legitimate users.
- Integration with SIEM and other security tools: Enables seamless data sharing and collaboration.
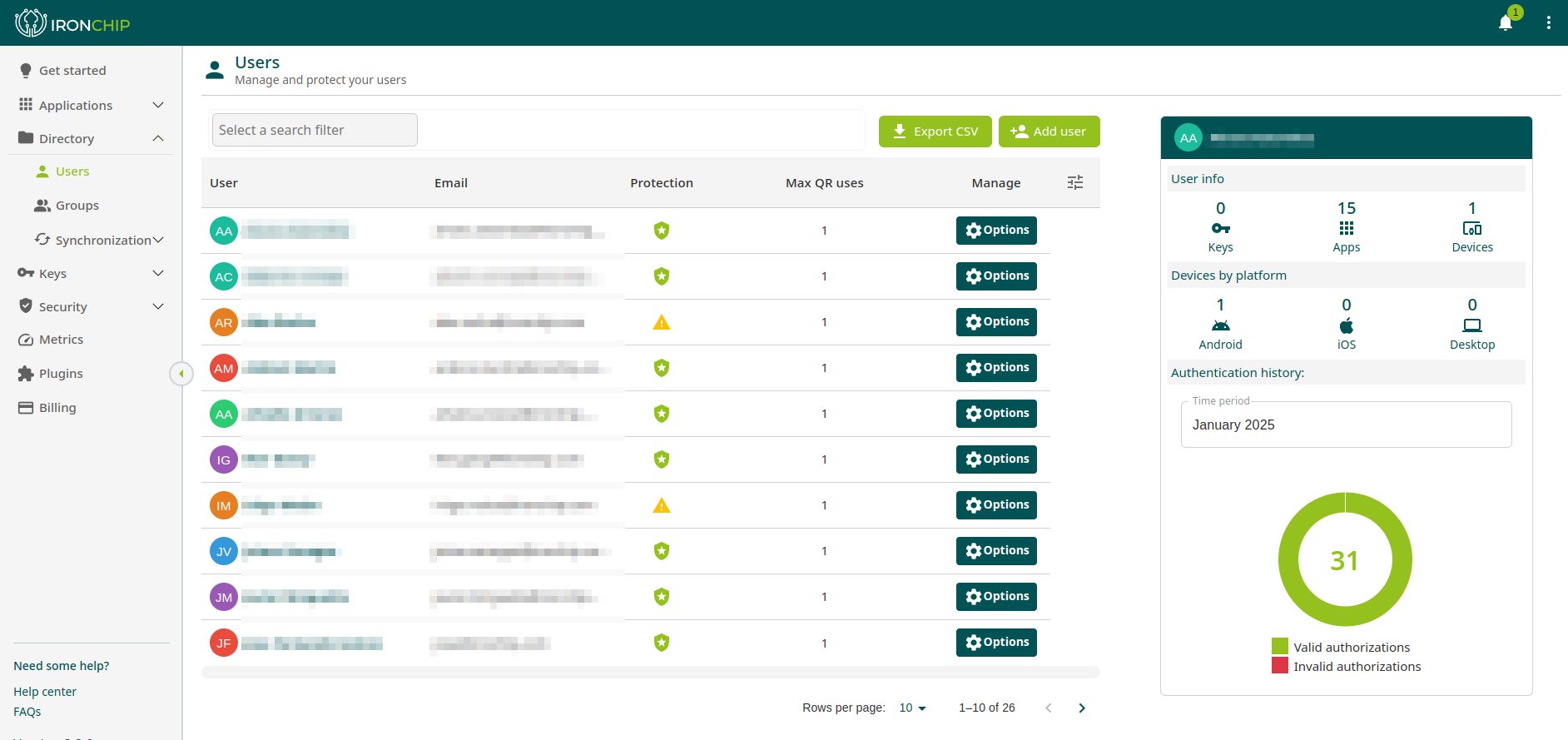
Identity
Streamlined Access, Simplified Management.
Managing passwords is a constant headache for IT departments. Ironchip eliminates this burden with passwordless authentication, offering:
- Centralized identity management: Manage all user identities from a single, unified platform.
- Elimination of password resets: Reduce help desk tickets and free up valuable IT resources.
- Seamless user onboarding and offboarding: Simplify the process of managing user access.
- No reliance on mobile phones for authentication (optional): Offers alternative authentication methods for users without mobile devices or in situations where mobile access is restricted.
- Flexible Deployment Options: Supports on-premise, cloud, and hybrid deployments to fit various IT infrastructures.
- Easy Integration: Integrates seamlessly with existing identity providers and applications using standard protocols.
- Granular Access Control: Provides fine-grained control over user access to resources.
- Detailed Logging and Auditing: Offers comprehensive logs for security analysis and compliance reporting.