Identity Platform
Identity Threat Detection & Response
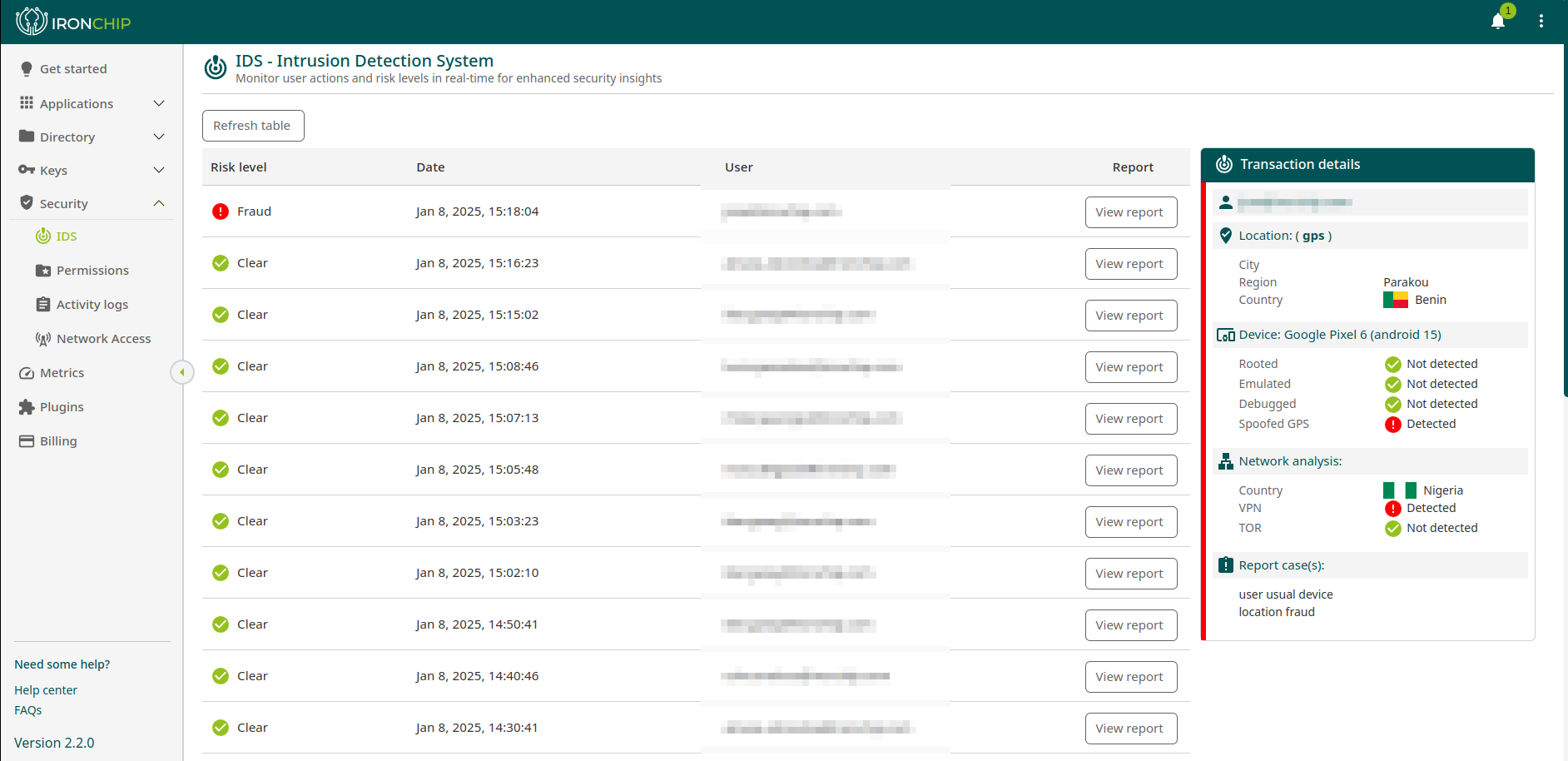
Cybercriminals increasingly target user identities to gain access to sensitive data and systems. Traditional security solutions often fall short in detecting and responding to these identity-based attacks. Ironchip ITDR addresses this gap by providing in-depth visibility and control over user activity.

ADVANTAGES
- Proactive Threat Detection: Identifies and stops identity-based attacks before they cause damage.
- Reduced Risk of Account Takeover: Prevents unauthorized access to user accounts and sensitive data.
- Improved Visibility into User Activity: Provides detailed insights into user behavior and access patterns.
- Faster Incident Response: Automates responses to suspicious activity, minimizing the impact of security incidents.
- Reduced False Positives: Leverages contextual data to improve the accuracy of threat detection and minimize disruptions for legitimate users.
- Enhanced Compliance: Helps meet regulatory requirements for identity and access management.
- Complements Existing Security Infrastructure: Works seamlessly with existing security tools and technologies.
Use Cases
- Detecting Insider Threats: Identifies suspicious activity by employees or contractors.
- Preventing Account Takeover: Blocks unauthorized access to user accounts.
- Securing Remote Access: Protects against unauthorized access from remote locations.
- Monitoring Privileged Access: Tracks and controls access by privileged users to sensitive systems.
- Detecting Lateral Movement: Identifies suspicious activity that indicates an attacker has gained access to the network and is moving laterally.