The power of location The freedom of passwordless
Next Generation Passwordless identity
Future is here
Meet the world's easier and secure identity & access management solution
- Passwordless Authentication
- Anti-Phishing Security
- Intrusion Threat Detection and Response (ITDR)
- Mobileless Authentication
- USB Authentication
- Agentless Authentication
- Integrable with Any Product

Eliminate Passwords, Elevate Security
The Power of Passwordless Authentication
Say goodbye to the risks and hassles of traditional passwords, drastically reducing the attack surface and enhancing security. This not only strengthens security but also improves user experience significantly.

Unbreakable Defense Against Phishing
Mutual Authentication
Our solution implements mutual authentication, an advanced security mechanism that verifies the identity of both the user and the server. This creates an impenetrable barrier against phishing attacks, where attackers attempt to impersonate legitimate websites to steal credentials. By requiring authentication from both parties, we ensure that connections are only established with legitimate servers, protecting users from deception and fraud.
Proactive Protection Against Scams
Intrusion Threat Detection and Response
Our ITDR system constantly monitors activity for suspicious patterns that may indicate a scam attempt or unauthorized access. Upon detecting a threat, the system responds automatically, blocking access, alerting the user and the security team, and preventing potential damage. This proactive security layer minimizes the risk of falling victim to scams and protects the integrity of accounts.
Secure Access on Any Device
Mobile and Desktop Authentication Agents
We offer native authentication agents for mobile devices (iOS and Android) and desktops (Windows, macOS, and Linux), facilitating a seamless and secure user experience. These agents enable quick and easy authentication using biometrics, push notifications, or security keys, eliminating the need for passwords. Multi-platform compatibility ensures secure access from any device.

Reinforced Physical Security
USB Security Key Authentication
For those seeking an additional layer of physical security, we offer support for USB security keys. These keys provide robust, phishing-resistant two-factor authentication. By requiring the physical presence of the key to authorize access, an extra layer of protection is added against unauthorized access.
Simplified Integration
Agentless Authentication
For environments where agent installation is not possible or desirable, we offer an agentless authentication solution. This option enables quick and easy integration with web applications and services using standard protocols like SAML, OAuth, or OpenID Connect. Agentless authentication simplifies deployment and reduces administrative overhead without compromising security.
Universal Compatibility
Integration with Standard Protocols
Our passwordless identity platform seamlessly integrates with any environment thanks to its compatibility with industry-standard protocols such as SAML, OAuth, OpenID Connect, RADIUS, and others. This flexibility allows for easy integration with existing applications and services without requiring complex modifications. Interoperability with different systems ensures smooth adoption and centralized identity management.
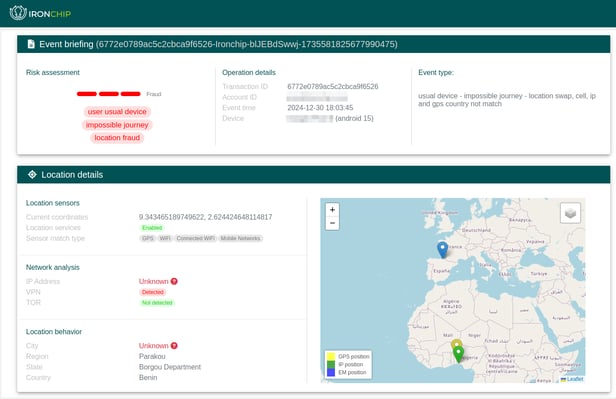
Beyond traditional detection
location intelligence gives you a complete view of risk and superior protection.
FREE
Enable passwordless authentication to seamlessly integrate and configure access to your services, endpoints and applications.
Authentication:
- Agentless Authenticator
- Computer Authenticator
- Mobile Authenticator
Identity & Access Management:
- Users, groups & devices management
- 1-10 users
Plugins:
- NPS Plugin
- Microsoft ADFS Plugin
Security:
- Access logs
Metrics & Others:
- Basic metrics
Enterprise
Passwordless authentication enhances security with advanced configuration and monitoring features. Includes standard capabilities, plus:
Authentication:
- USB Token Authenticator
- Smartcard Authenticator
Identity & Access Management:
- Automatic provision from other directories i.e. Acitve Directory
- Configure conditional access policies
Plugins:
- LDAP Server
- Windows, Linux & MAC Logon
Security:
- Permissions Management
- Configurable IP whitelist
- Activity logs
Metrics & others:
- Realtime timeline
- Corporative Look&Feel
Premium
The Ironchip's identity full experience to zero account takeover
Authentication:
- Location-based autentication
- Context-based autentication
Identity & Access Management:
- Secure location Management
- Generate corporate perimeter of trust
Intrusion Threat Detection 6 Response:
- Detect identity threats
- Define customized risk rules based on the context
- Block attacks automatically
- Get realtime reports via API
Metrics & others:
- Advanced metrics
- Syslog / API for SIEM integration
"Ironchip implements its product at a key point of authentication in a simple, cost-effective manner, combined with a user experience that is hard to find nowadays."
Fátima Cereijo
Fraud Control and Privacy Manager at Abanca
"This solution stands out as a remarkable alternative, combining security and simplicity, to carry out authentications through MFA in various applications."
Edorta Guerrero
IT Systems Administrator & Business Intelligence Reporting Analyst at GHI Smart Furnaces
"We consider it a company that is constantly evolving and growing, based on customer needs to meet their expectations."
Systems Administration
Nalanda