The power of location The freedom of transparency
Next Generation Fraud detection
Future is here
Meet the world's easier and secure identity & access management solution
- Location Intelligence
- Account Takeover Detection
- New Account Fraud Detection
- Malware Detection
- Custom Rules
- Money Laundering Detection
- Fraud Hotspots Detection
- Fraud Case Manager
- User Device & Location Forensic Analysis
- Scam & Authorized Fraud Detection
The All-Seeing Eye
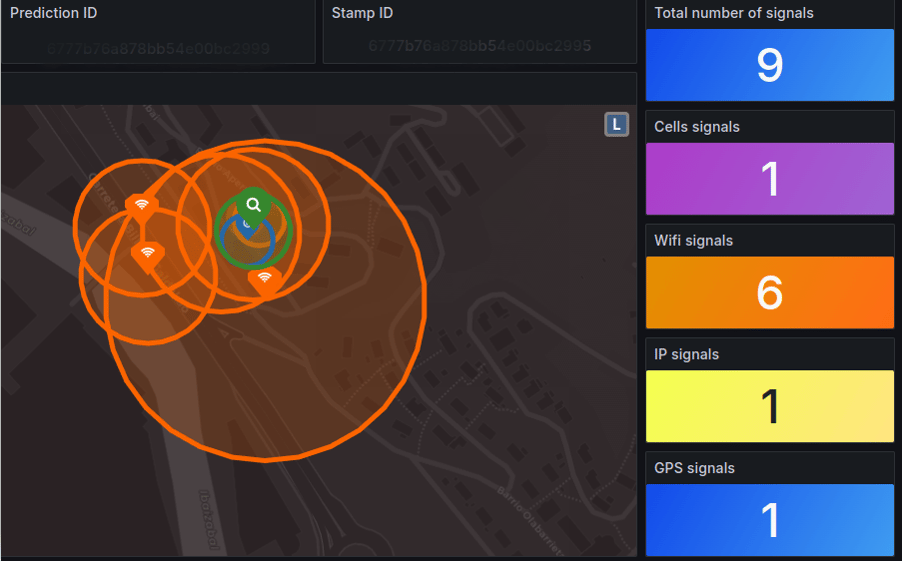
Location Intelligence
Unleash the power of real-time location analysis to anticipate and neutralize fraudulent activity. Our system deciphers intricate behavioral patterns, flagging impossible travel scenarios, sudden location shifts, and other anomalies invisible to conventional security measures. Step into the future of fraud prevention.
The Unbreachable Firewall
Account Takeover Detection
Fortify your digital perimeter with relentless login activity monitoring. By comparing historical data and identifying suspicious access attempts from unknown devices or locations, our system acts as an impenetrable shield against identity theft. Secure your kingdom.
The First Line of Defense Against Synthetic Identities
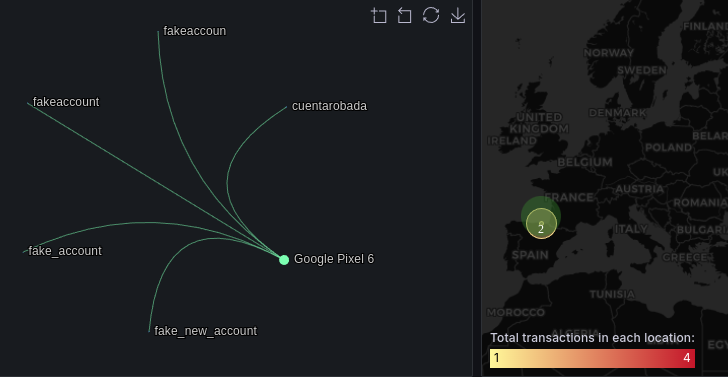
New Account Fraud Detection
Preemptively thwart fraudulent account creation with our advanced identity verification. By meticulously examining registration data, including location, we expose synthetic identities and prevent downstream fraud, safeguarding your ecosystem from the outset.
The Silent Guardian Against Cyber Threats
Malware Detection
Integrate cutting-edge malware detection capabilities to identify and quarantine malicious software lurking on user devices. Prevent credential theft, data breaches, and system compromise with our proactive malware defense.
Tailored Security for a Dynamic Threat Landscape
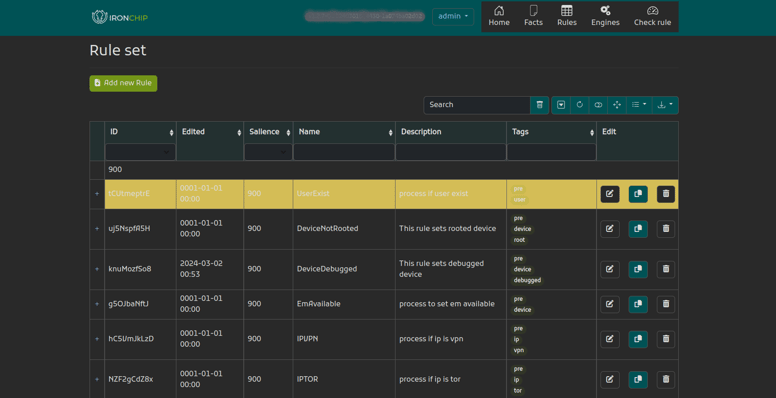
Custom Rules
Command your security posture with fully customizable rules based on your unique business needs. Define risk thresholds, pinpoint suspicious behavioral patterns, and automate responses for an adaptive defense that evolves with the threat landscape.
Unmasking the Shadows of Illicit Finance
Money Laundering Detection
Decrypt the complex web of financial crime with advanced transaction analysis and location-based insights. Our system detects suspicious activities indicative of money laundering, empowering you to comply with regulations and protect your financial integrity
Mapping the Battleground Against Fraud
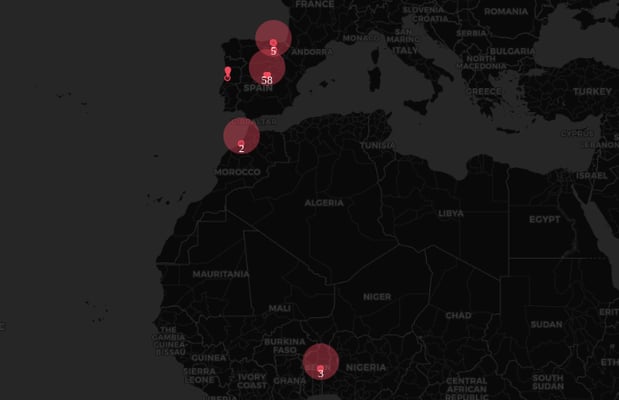
Fraud Hotspots Detection
Visualize the concentration of fraudulent activity with dynamic geographic mapping. Identify high-risk zones, deploy targeted security measures, and preemptively disrupt emerging fraud trends. Stay ahead of the curve.
Orchestrating the Fight Against Fraud
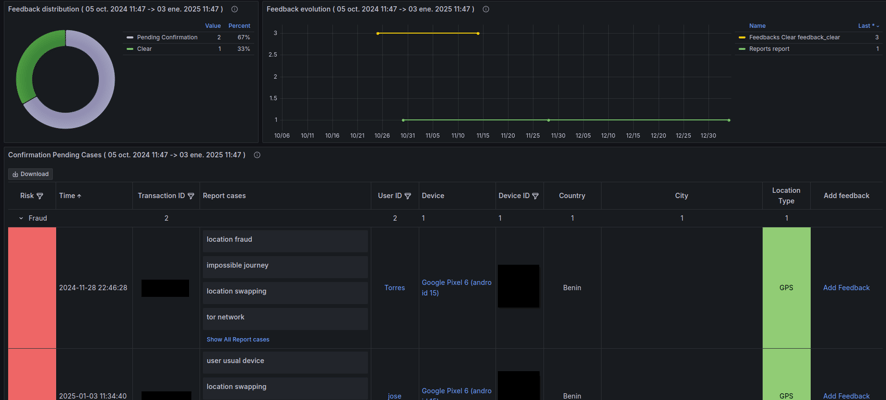
Fraud Case Manager
Centralize your fraud investigations with our powerful case management platform. Streamline workflows, facilitate team collaboration, and generate comprehensive reports for efficient incident resolution and data-driven decision-making. Take control of the narrative.
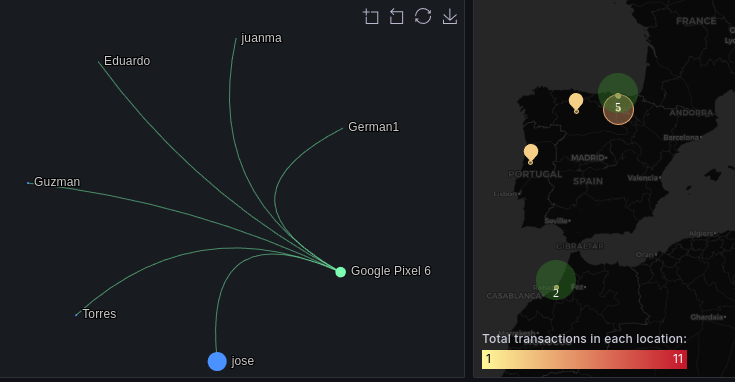
Unveiling the Hidden Truth
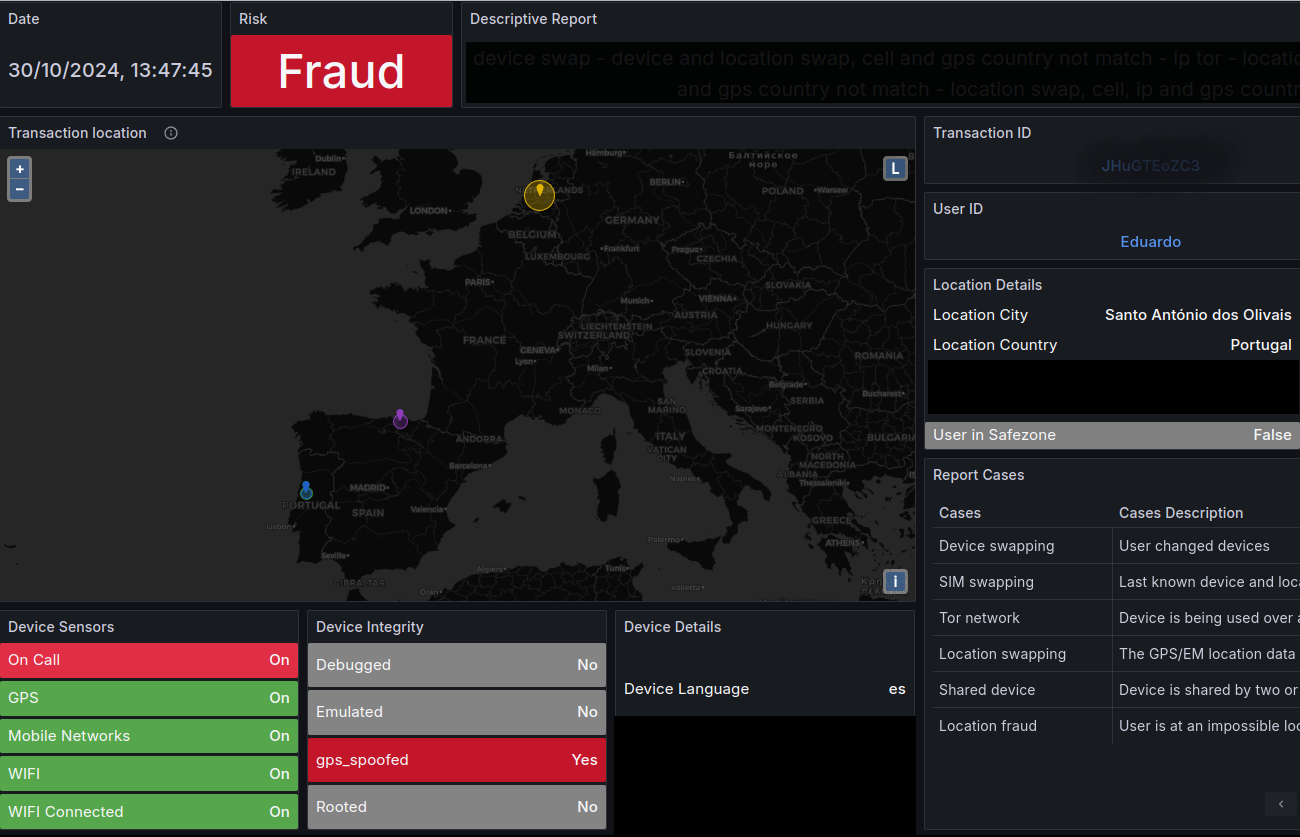
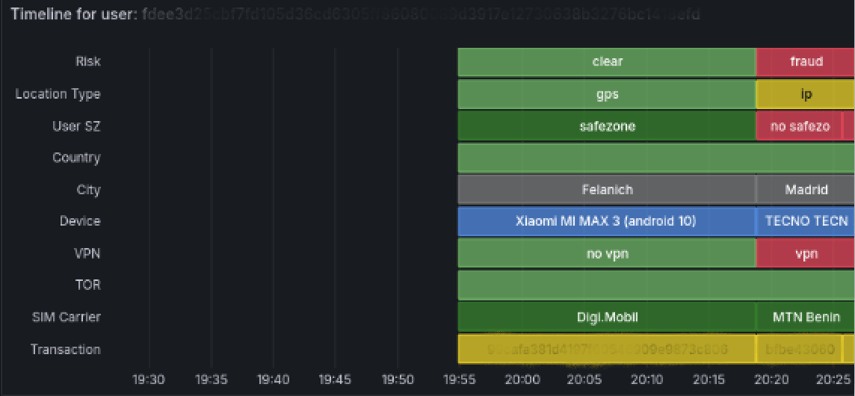
User Device & Location Forensic Analysis
Delve into the digital underworld with granular forensic analysis of user devices and locations involved in fraudulent activities. Unearth critical evidence, reconstruct attack vectors, and empower informed responses with unparalleled investigative insights.

The Ultimate Shield Against Digital Deception
Scam & Authorized Fraud Detection
Safeguard your users from the ever-evolving landscape of digital scams. Our system detects phishing, smishing, vishing, and other social engineering tactics, protecting your community from manipulation and financial loss.
Beyond traditional detection
location intelligence gives you a complete view of risk and superior protection.
GATHER
Empower your operations with real-time, multi-source data collection and intuitive visualization for foundational insights.
Data collection:
- Location data
- User data
- Device data
- Browser data
- Application data
- Network data
Data enrichment and intelligence:
- Location intelligence
- Ironchip's location
Toolset
- Visualization dashboard
Real-time data retrieval
- HTTP API
- Webhook
Data retention
- 3 month data retention
UNDERSTAND
Transform raw data into actionable intelligence with advanced enrichment, comprehensive analytics, and preliminary fraud detection.
- Includes GATHER tier
Data enrichment and intelligence:
- Location intelligence
- Ironchip's location
- Network location
- Electromagnetic location
- GPS location
- User intelligence
- Device intelligence
- Browser intelligence
- Application intelligence
- Network intelligence
Fraud prevention:
- Location tampering
- Device tampering
- Blocklist and Allowlist
Toolset
- Visualization dashboard
- Forensic analysis dashboard
- Custom rules & logic
Real-time data retrieval
- HTTP API
- Webhook
- Websocket
Data retention
- Extended data retention up to 12 months
INTERCEPT
Proactively safeguard your assets with end-to-end fraud prevention, extended analytics, and robust threat mitigation capabilities.
- Includes UNDERSTAND tier
Fraud prevention:
- Location tampering
- Device tampering
- Blocklist and Allowlist
- Malware detection
- Account takeover
- Synthetic identity
- Money laundering
- Shared intelligence
Toolset
- Visualization dashboard
- Forensic analysis dashboard
- Custom rules & logic
- Fraud case manager
- Data lake & analytics
Real-time data retrieval
- HTTP API
- Webhook
- Websocket
Data retention
- Extended data retention up to 24 months
"Ironchip implements its product at a key point of authentication in a simple, cost-effective manner, combined with a user experience that is hard to find nowadays."
Fátima Cereijo
Fraud Control and Privacy Manager at Abanca
"This solution stands out as a remarkable alternative, combining security and simplicity, to carry out authentications through MFA in various applications."
Edorta Guerrero
IT Systems Administrator & Business Intelligence Reporting Analyst at GHI Smart Furnaces
"We consider it a company that is constantly evolving and growing, based on customer needs to meet their expectations."
Systems Administration
Nalanda